Abstract — This blog talks about the critical challenges due to Data Security, Privacy of Data and Local Law and Jurisdiction where Data is held; in a practical Cloud Computing environment based implementation. I tried covering some un-touched area of concern into my paper, like – Governance, Compliance, Trust, Architecture and Architectural Changes, Identity and Access, Isolation, Protection, Availability and Responsiveness. In fact I preferred discussing the more pressing issue than standard – the issue of Jurisdiction. Ultimately I have concluded this paper by raising the serious concerns about primary issues of cloud computing and talked about the accountability, that who should take it forward with initial checks and validation.
I. Introduction
The Data Security, Privacy and Jurisdiction concern in Cloud Computing has been in question from day one. Data Security and Privacy is tightly coupled with Jurisdiction of data or the local law and jurisdiction where data is held. If the Cloud Computing can insure the Data Security and Privacy of your data then that can be the game changer of the whole computing scenario. It is not limited to the Public Cloud, but it is important for Private/ Hybrid or Community Cloud as well. The key security and privacy concern can be addressed by focusing on following vital aspects:
- Governance and Control over Policy, Procedure and Standards
- Compliance with Data Location and Law of Land
- Trust with Visibility
- Architecture that is not Attack Prone
- Identity and Access Management
- Software Isolation
- Data Protection
- Availability Assurance based on Value Concentration
- Incident Responsiveness
What Cloud Computing exactly mean? I would like to define Cloud Computing as “A style of computing through which we can model and extend our service for a Secured, Convenient and On-demand network access to a shared pool of computing resources like software, platform and infrastructure that may include network, servers, storage, applications and various associated services.” Here I should not miss the opportunity to discuss a technology that complements Cloud Computing a lot; it is as good as the other side of the coin where one side is Cloud. Please see my elaboration on the Virtualization sub-principle in a separate section of this paper. This cloud model promotes availability and is composed of: 5 Essential Characteristics
- On-demand self-service
- Measured service
- Broad network access
- Resource pooling
- Rapid elasticity
3 Service Models
4 Deployment Models
- Public Cloud
- Private Cloud
- Hybrid Cloud
- Community Cloud
II. Fact and Figures:
Gartner Executive Programs Worldwide Survey of More Than 2,000 CIOs Identifies Cloud Computing as Top Technology Priority for CIOs in 2011 TABLE I. Top 10 Technology Priorities in 2011a
| Table Head |
Latest Top 10 Technology Priorities |
| Top 10 Technology Priorities |
Ranking 2011 (Latest) |
Ranking 2010 (Previous) |
|
Cloud computing |
1 |
2 |
|
Virtualization |
2 |
1 |
|
Mobile technologies |
3 |
6 |
|
IT management |
4 |
10 |
|
Business intelligence |
5 |
5 |
|
Networking, voice and data communications |
6 |
4 |
|
Enterprise applications |
7 |
N/Ab |
|
Collaboration technologies |
8 |
N/Ab |
|
Infrastructure |
9 |
N/Ab |
|
Web 2.0 |
10 |
3 |
a. Source: Gartner EXP b. It was not in the range of top 10 in 2010 rating N.B. – We can notice that Cloud Computing jumped from 2nd to 1st position. Virtualization slipped from 1st to 2nd. BI maintained its last position. Web 2.0 Slipped from 3rd to 10th. Comparison is between 2010 Vs 2011 Gartner data. TABLE I. Companies With Active Private Cloudsa
| Table Head |
Companies With Active Private Clouds |
|
2011 (Latest) |
2010 (Previous) |
|
Companiesb (With Active Private Clouds) |
37% |
29% |
a. Source: Unisphere Research b. (In production, limited use, or pilot stage—2010 to 2011) TABLE II. Companies using public clouda
| Table Head |
Companies Using Public Clouds |
|
2011 (Latest) |
2010 (Previous) |
|
Companies (Using Public Clouds) |
21% |
14% |
a. Source: Unisphere Research
III. Local Law and Jurisdiction where data is held
Once we talk about Jurisdiction in this context, the first thing which comes to our mind is, the Local Law and Jurisdiction where data is held. In fact I preferred discussing the more pressing issue than standard, the issue of Jurisdiction first because of its current context, the matter of most of the debates in Cloud Computing Scenario, especially in case of Public Cloud (however it can’t be ignored even in case of Private clouds where practically the data is at different geographical location). Data that might be secure in one country may not be secure in another. In many cases though, users of cloud services don’t know where their information is held. In the process of standardizing the data laws of its member states, the EU favors very strict protection of privacy, while in America laws such as the US Patriot Act invest government and other agencies with virtually limitless powers to access information including that belonging to companies. It has been noticed that most of the Asian Countries either have not any such law or having very low intense or ineffective law to protect IT data in such cloud computing environment. European concerns about US privacy laws led to creation of the US Safe Harbor Privacy Principles, which are intended to provide European companies with a degree of insulation from US laws. Cloud providers are becoming more sensitive to legal and regulatory concerns, and may be willing to commit to store and process data in specific jurisdictions and apply required safeguards for security and privacy. However, the degree to which they will accept liability for exposure of content under their control remains to be seen. Even so, organizations are ultimately accountable for the security and privacy of data held by a cloud provider on their behalf.
IV. Virtualization
The heart of virtualization is abstraction, or a loose coupling between service requestors and the services themselves. Requests are satisfied from pools of resources that are invisible to the requestor and can be dynamically adjusted according to need.
Reconfiguring resources, according to demand, is key to effective IT architecture. In recent years, the focus has been on creating virtualized pools of CPU servers, for example VMware or Oracle Virtual Machine. This is a very effective technique for improving CPU utilization and handling fluctuating demand across heterogeneous workloads. However, just focusing on the CPU layer is insufficient. Performance bottlenecks and single points of failure can occur at any layer in the architecture. A balanced system needs virtualization applied to all the layers. Many critical elements—including storage disks, database servers, application servers, and web servers—all need to be deployed as pools of resources that can be dynamically scaled and configured for failover/failback. Virtualization and Clustering are the two key technologies that make up Grid Computing. These technologies are complementary. Cloud Computing is NOT just server virtualization. Clustering is also an important enabler to cloud computing. Virtualization: makes a single computer look like many computers.
- The size and power are variable/ configurable.
- Virtual machines can be migrated without downtime
- Virtual machines enable far more detailed accounting of which applications, LOBs, customers are using IT resources.
Database or Middleware Clustering is also a type of virtualization. It makes many computers (or even virtual machines) look like a single resource.
- Huge databases and middleware tiers can be built using powerful, low-cost, high volume components (like blades or rack servers)
- Redundancy of clusters enables high-performance and scalability through parallel operations
- Redundancy also enables inherent high availability, as clusters can survive one or more node failures
V. Data Security and Privacy
Data Security has become a mainstream concern with well-established governance and compliance, increasing public awareness and more business processes going online. Security is an integral part of every business process. Everyone discuss about it saying that it must be built into the systems, applications and networks and further protected by physical and managerial controls. Every breached security system was once thought infallible – SaaS (software as a service) and PaaS (platform as a service) providers all trumpet the robustness of their systems, often claiming that security in the cloud is tighter than in most enterprises. But the simple fact is that every security system that has ever been breached was once thought infallible.
“One of the world’s largest technology companies, Google, has invested a lot of money into the cloud space, where it recognizes that having a reputation for security is a key determinant of success. “Security is built into the DNA of our products,” says a company spokesperson. “Google practices a defense-in-depth security strategy, by architecting security into our people, process and technologies”. However, the cloud is still very much a new frontier with very little in the way of specific standards for security or data privacy0.”
Google was forced to make an embarrassing apology previously when its Gmail service collapsed in Europe, while Salesforce.com is still smarting from a phishing attack couple of years back which duped a staff member into revealing passwords. While cloud service providers face similar security issues as other sorts of organizations, analysts warn that the cloud is becoming particularly attractive to cyber crooks. “The richer the pot of data, the more cloud service providers need to do to protect it,” says IDC research analyst David Bradshaw0. Securing the perimeter is no longer sufficient as data theft often occurs with help from insiders. Here I am not going to discuss Data Vault, Identity and Access Management, VPD – Virtual Private Database etc., because there all are well known and old method of handing Data Security and Privacy issue. Issues of management, accountability and operational strategy are evolving quickly; but no one has talked about a security solution that is in the hand of the client not the cloud service provider. I would like to introduce a solution for that as “The LOGICAL Data Security Layer”1. I will talk about LOGICAL data security and its algorithm and architecture at high level in this paper2. You can read my detailed paper on the same named ‘LOGICAL Data Security Layer for Cloud Computing’3. 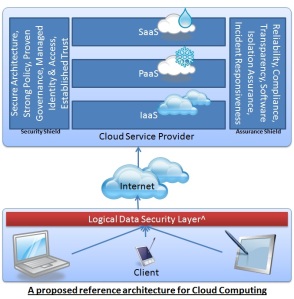 Logical Data Security Layer is an arrangement to safeguard your valued business data. It is very easily implementable for Additive and Semi-Additive nature of data but it can also be implemented with data of different types like Date/Char etc using control structures or Meta data structures or by using structured repository. It is also applicable for Non-Additive data but bit tricky for calculated Non-Additive data4. This layer allows you to logically tweak the up-stream and down-stream business data. It is recommended if this processed is followed at client side itself, and it should take place before the data goes up to the cloud from your application. Actually this layer will seat between the application and the DB. It is always recommended to use this method on atomic data, the data which is not getting calculated within the data base on the fly (say by using some trigger); or better not to use this method if the situation is like this: Where Column1 data and Column2 data is used to calculate and save Column3 data. It is always recommended to use in a scenario where any such data is calculated only during generation of any such required reports. It should be noted that the whole methodology of Logical Data Security Layer actually resides into your Middle Layer or Business Layer. It should be governed between the application and DB. In this method, every Application to DB inbound data should be tweaked based on the underlying rules defined by the client/business and every DB to Reporting outbound data should be neutralized by adequate adjustment. I tried classifying this Logical Data Security Methodology in three logical groups and subsequent sub-groups:
Logical Data Security Layer is an arrangement to safeguard your valued business data. It is very easily implementable for Additive and Semi-Additive nature of data but it can also be implemented with data of different types like Date/Char etc using control structures or Meta data structures or by using structured repository. It is also applicable for Non-Additive data but bit tricky for calculated Non-Additive data4. This layer allows you to logically tweak the up-stream and down-stream business data. It is recommended if this processed is followed at client side itself, and it should take place before the data goes up to the cloud from your application. Actually this layer will seat between the application and the DB. It is always recommended to use this method on atomic data, the data which is not getting calculated within the data base on the fly (say by using some trigger); or better not to use this method if the situation is like this: Where Column1 data and Column2 data is used to calculate and save Column3 data. It is always recommended to use in a scenario where any such data is calculated only during generation of any such required reports. It should be noted that the whole methodology of Logical Data Security Layer actually resides into your Middle Layer or Business Layer. It should be governed between the application and DB. In this method, every Application to DB inbound data should be tweaked based on the underlying rules defined by the client/business and every DB to Reporting outbound data should be neutralized by adequate adjustment. I tried classifying this Logical Data Security Methodology in three logical groups and subsequent sub-groups:
- Flat Method:
- Algorithmic Tweaking – Follow some standard, non-standard or in-house grown algorithm.
- Classified Tweaking – i.e. Dept wise/ region wise/ geography wise etc.
- Seasonal Method:
- Periodic – Weekly/ monthly/ quarterly/ financial period wise etc.
- Conditional – e.g. If more than 1000 then ‘x’ else ‘y’ etc.
- Specialized Method:
e.g. Date Tweaking Character / Text Tweaking
- Business Keyword Tweaking
- LoV (List of Values Tweaking)
- Vital Master Info Tweaking
- Algorithmic Data Scrambling – So that it can be recovered as and when required; better for text and large text.
This decision of selecting the right methodology should be 100% subjective and based on the Nature of the Business, its Data and the underlying Business Priorities.
VI. The Upside
While the biggest obstacle facing cloud computing is security, the cloud computing paradigm provides opportunities for innovation in provisioning security services that hold the prospect of improving the overall security of some organizations. The biggest beneficiaries are likely to be smaller organizations that have limited numbers of information technology administrators and security personnel, and lack the economies of scale available to larger organizations with sizeable data centers. Potential areas of improvement where organizations may derive security benefits from transitioning to a public cloud computing environment include the following:
- Platform Strength: The structure of cloud computing platforms is typically more uniform than that of most traditional computing centers. Greater uniformity and homogeneity facilitate platform hardening and enable better automation of security management activities like configuration control, vulnerability testing, security audits, and security patching of platform components.
- Resource Availability: The scalability of cloud computing facilities allows for greater availability. Redundancy and disaster recovery capabilities are built into cloud computing environments and on-demand resource capacity can be used for better resilience when facing increased service demands or distributed denial of servattacks, and for quicker recovery from serious incidents.
- Staff Specialization: Cloud providers, just as organizations with large-scale computing facilities, have an opportunity for staff to specialize in security, privacy, and other areas of high interest and concern to the organization.
- Backup and Recovery: The backup and recovery policies and procedures of a cloud service may be superior to those of the organization and, if copies are maintained in diverse geographic locations, may be more robust. Data maintained within a cloud can be more available, faster to restore, and more reliable in many circumstances than that maintained in a traditional data center.
- Mobile Endpoints: The architecture of a cloud solution extends to the client at the service endpoint, used to access hosted applications. Cloud clients are generally lightweight and can be browser-based or applications-based1.
- Data Concentration: Data maintained and processed in the cloud can present less of a risk to an organization with a mobile workforce than having that data dispersed on portable computers or removable media out in the field, where theft and loss of devices routinely occur.
Besides providing a computing platform or substitute for in-house applications, following can also be focused on provisioning security to other computing environments:
- Data Center Oriented: Cloud services can be used to improve the security of data centers. For example, electronic mail can be redirected to a cloud provider via mail exchange (MX) records, examined and analyzed collectively with similar transactions from other data centers to discover widespread spam, phishing, and malware campaigns, and to carry out remedial action (e.g., quarantining suspect messages and content) more comprehensively than a single organization would be able to do. Researchers have also successfully demonstrated system architecture for provisioning cloud-based antivirus services, as an alternative to host-based antivirus solutions.
- Cloud Oriented: Cloud services are available to improve the security of other cloud environments. For example, reverse proxy products are available that enable unregulated access to a SaaS environment, yet maintain the data stored in that environment in encrypted form. Cloud-based identity management services also exist, which can be used to augment or replace an organization’s directory service for identification and authentication of users to a cloud.
VII. The Downside
Besides its many potential benefits for security and privacy, cloud computing also brings with it potential areas of concern, when compared with computing environments found in traditional data centers. Some of the more fundamental concerns include the following:
- System Complexity: A public cloud computing environment is extremely complex compared with that of a traditional data center. Many components comprise a public cloud, resulting in a large attack surface. Besides components for general computing, such as deployed applications, virtual machine monitors, guest virtual machines, data storage, and supporting middleware, there are also components that comprise the management backplane, such as those for self-service, resource metering, quota management, data replication and recovery, workload management, and cloud bursting.
- Shared Multi-tenant Environment: Public cloud services offered by providers have a serious underlying complication – subscribing organizations typically share components and resources with other subscribers that are unknown to them. Threats to network and computing infrastructures continue to increase each year and have become more sophisticated. Having to share an infrastructure with unknown outside parties can be a major drawback for some applications and requires a high level of assurance for the strength of the security mechanisms used for logical separation.
Please remember an attacker could also pose as a subscriber to exploit vulnerabilities.
- Internet-facing Services: Public cloud services are delivered over the Internet, exposing both the administrative interfaces used to self-service an account and the interfaces for users and applications to access other available services. Applications and data that were previously accessed from the confines an organization’s intranet, but moved to the cloud, must now face increased risk from network threats that were previously defended against at the perimeter of the organization’s intranet and from new threats that target the exposed interfaces.
- Loss of Control: While security and privacy concerns in cloud computing services are similar to those of traditional non-cloud services, they are amplified by external control over organizational assets and the potential for mismanagement of those assets. Migrating to a public cloud requires a transfer of control to the cloud provider over information as well as system components that were previously under the organization’s direct control. Loss of control over both the physical and logical aspects of the system and data diminishes the organization’s ability to maintain situational awareness, weigh alternatives, set priorities, and effect changes in security and privacy that are in the best interest of the organization.
As with any technology, cloud computing services can be turned towards improper or illicit activities. A couple of noteworthy instances have already occurred that give a sense of what might be expected in the future:
- Botnets: In many ways, botnets assembled and controlled by hackers are an early form of cloud computing. Cost reduction, dynamic provisioning, redundancy, security, and many other characteristics of cloud computing apply. Botnets have been used for sending spam, harvesting login credentials, and launching injection attacks against Websites. Botnets could be used to launch a denial of service attack against the infrastructure of a cloud provider. The possibility that a cloud service could become infiltrated by a botnet has already occurred; in 2009, a command-and-control node was discovered operating from within an IaaS cloud. Spammers have also purchased cloud services directly and launched phishing campaigns, ensnaring recipients with malware via social engineering techniques.
VIII. Key Issues
- Policy – The word policy could have a number of meanings as it is used in conjunction with IT architecture and systems. For example, it could mean governance relating to software architecture development and implementation; or it could mean Compliance, Operational rules and Standards for administering a deployed production system; or Data Location Policy or even Electronic Data Storage Policy etc.
- Governance – It implies control over policies, procedures and standards. With the wide availability of cloud computing services, lack of organizational controls over employees and any other agencies engaging such services randomly can be a source of problems. In fact the Cloud computing amplifies the need of Governance. More than anything else, good governance is the key enabler of cloud computing.
- Compliance – It involves conformance with an established specification, standard, regulation, or law. Various types of security and privacy laws and regulations exist within different countries at the national, state, and local levels, making compliance a potentially complicated issue for cloud computing.
- Data Location – The detailed information about the location of an organization’s data is unavailable or not disclosed to the service subscriber by many Cloud computing services provider. This situation makes it difficult to ascertain whether sufficient safeguards are in place and whether legal and regulatory compliance requirements are being met. External audits and security certifications can to some extent alleviate this issue, but they are not a universal remedy.
When information crosses borders, the governing legal, privacy, and regulatory regimes can be ambiguous and raise a variety of concerns. Remember the LAW-OF-LAND.
- Electronic Data Storage Efficiency and Technical Capability – That involves the identification, collection, processing, analysis, and production of electronic documents in the discovery phase of litigation.
The capabilities and process of a cloud provider; For example, a cloud provider’s archival capabilities may not preserve the original metadata as expected, causing spoliation (i.e., the intentional, reckless, or negligent destruction, loss, material alteration, or obstruction of evidence that is relevant to litigation), which could negatively impact litigation.
- Trust worthiness – An organization hands over direct control over many aspects of security and, in doing so, confers an unprecedented level of trust onto the cloud provider.
- Insider Access – Insider Access threats go beyond those posed by current or former employees to include contractors, organizational affiliates, and other parties that have received access to an organization’s networks, systems, and data to carry out or facilitate operations.
Moving data and applications to a cloud computing environment operated by a cloud provider expands the insider security risk not only to the cloud provider’s staff, but also potentially among other customers using the service.
- Data Ownership – Data ownership definition should be in Black and White. Ideally, the contract should state clearly that the organization retains ownership over all its data; that the cloud provider acquires no rights or licenses through the agreement to use the data for its own purposes, including intellectual property rights or licenses; and that the cloud provider does not acquire and may not claim any security interest in the data. For these provisions to work as intended, the terms of data ownership must not be subject to unilateral amendment by the cloud provider.
- Composite Services – In case of sub-contracting or third party outsourced cloud services; trust is often not transitive, requiring that third-party arrangements be disclosed in advance of reaching an agreement with the cloud provider.
- Visibility and Transparency – Transparency in the way the cloud provider operates is a vital ingredient for effective oversight over system security and privacy by an organization. To ensure that policy and procedures are being enforced throughout the system lifecycle, service arrangements should include some means for gaining visibility into the security controls and processes employed by the cloud provider and their performance over time.
- Risk Management – Risk management is the process of identifying and assessing risk, and taking the necessary steps to reduce it to an acceptable level.
Assessing and managing risk in systems that use cloud services can be a challenge. To the extent practical, the organization should ensure that security controls are implemented correctly, operate as intended, and meet its security requirements. Establishing a level of trust about a cloud service is dependent on the degree of control an organization is able to exert on the provider to provision the security controls necessary to protect the organization’s data and applications, and also the evidence provided about the effectiveness of those controls.
- Secure Architecture – The architecture of the software systems used to deliver cloud services comprises hardware and software residing in the cloud.
Many of the simplified interfaces and service abstractions contradict the inherent complexity that affects security. The complexity in virtual machine environments can also be more challenging than their traditional counterparts, giving rise to conditions that undermine security. The hypervisor or virtual machine monitor, Virtual Network Protection, Ancillary Data are some of the aspects which should be addressed with intense emphasis while architecting the whole cloud. Client-Side Protection and Server-Side Protection should not be compromised at any cost, because these are the two edges of the whole arrangement.
- Identity and Access Management – Authentication and Access Control are two vital mechanism in Cloud Computing to check security.
- Isolation – Obviously, we are talking about Software Isolation here. High degrees of multi-tenancy over large numbers of platforms are needed for cloud computing to achieve the envisioned flexibility of on-demand provisioning of reliable services and the cost benefits and efficiencies due to economies of scale. To reach the high scales of consumption desired, cloud providers have to ensure dynamic flexible delivery of service and isolation of subscriber resources. Multi-tenancy in cloud computing is typically done by multiplexing the execution of virtual machines from potentially different users on the same physical server. It is important to note that applications deployed on guest virtual machines remain susceptible to attack and compromise, much the same as their non-virtualized counterparts.
- Data Protection – Data stored in the cloud typically resides in a shared environment collocated with data from other customers. Organizations moving sensitive and regulated data into the cloud, therefore, must account for the means by which access to the data is controlled and the data is kept secure.
- Data Isolation – Data can take many forms.
Access controls are one means to keep data away from unauthorized users; encryption is another. Data must be secured while at rest, in transit, and in use, and access to the data must be controlled. Currently, the responsibility for cryptographic key management falls mainly on the cloud service subscriber.
- Data Sanitization – The data sanitization practices that a cloud provider implements have obvious implications for security. Sanitization is the removal of sensitive data from a storage device in various situations. Data sanitization also applies to backup copies made for recovery and restoration of service, and also residual data remaining upon termination of service.
- Availability – In simple terms, availability is the extent to which an organization’s full set of computational resources is accessible and usable. Availability can be affected temporarily or permanently, and a loss can be partial or complete. Denial of service attacks, equipment outages, and natural disasters are all threats to availability. The concern is that most downtime is unplanned and can impact the mission of the organization. Hence need serious consideration of this fact.
- Incident Response – Incident response involves an organized method for dealing with the consequences of an attack against the security of a computer system. The cloud provider’s role is vital in performing incident response activities, including incident verification, attack analysis, containment, data collection and preservation, problem remediation, and service restoration. This requires periodic revision due to its importance in business continuity.
IX. The Whole Economics Of Cloud And Its Security
Cloud computing services benefit from economies of scale achieved through versatile use of resources, specialization, and other practicable efficiencies. However, cloud computing is an emerging form of distributed computing that is still in its infancy. Most companies today are under tremendous pressure to reduce costs wherever possible. IT budgets are traditionally targets for cost cutting initiatives. These cost cutting initiatives often lead to failed or partially implemented systems, often intended to replace aging systems, which were poorly integrated. Further exacerbating the problem, the systems that were being replaced were never retired, leading to functionality split between numerous applications, causing complex and sometimes manual processes to be implemented and maintained across the old and new systems. Major factors like Project Based System Implementations, Inorganic Growth (Growth through M&A) and Cost Reduction Efforts, along with the numerous other drivers of IT complexity have left companies in a state where 80% of IT budgets are spent just keeping the systems running, leaving only 20% being spent to support new business opportunities.  From a financial perspective, it has been found that simple chargeback models work well in many instances. e.g. A simple chargeback model can be derived as follows:
From a financial perspective, it has been found that simple chargeback models work well in many instances. e.g. A simple chargeback model can be derived as follows:  Reducing cost and increasing efficiency are primary motivations for moving towards a public cloud, but reducing responsibility for security should not be. Ultimately, the organization is accountable for the overall security of the outsourced service. Monitoring and addressing security issues that arise remain in the purview of the organization, and it does oversight over other important issues such as performance and availability. Because cloud computing brings with it new security challenges, it is essential for an organization to oversee and manage how the cloud provider secures and maintains the computing environment and ensures data is kept secure. The main advantage of using cloud computing facility economically and commercially is as follows:
Reducing cost and increasing efficiency are primary motivations for moving towards a public cloud, but reducing responsibility for security should not be. Ultimately, the organization is accountable for the overall security of the outsourced service. Monitoring and addressing security issues that arise remain in the purview of the organization, and it does oversight over other important issues such as performance and availability. Because cloud computing brings with it new security challenges, it is essential for an organization to oversee and manage how the cloud provider secures and maintains the computing environment and ensures data is kept secure. The main advantage of using cloud computing facility economically and commercially is as follows:
- It has low total cost of ownership.
- It has increased availability.
- Its faster application delivery capability.
- Due to its Flexible Model.
- It enables collaboration and community computing.
- It improved Business Continuity.
- It has Rental Pricing Model.
- It has reduced ongoing and life cycle costs.
- It is always on, always available.
- It helps expedite time to market; hence competitive advantage.
- It scales by demand, hence no wasted capacity.
- It provides platform for easier and faster information sharing and mobile workforce.
X. Conclusion
The Cloud computing promises to have far-reaching effects on the systems and networks of almost every segment of organization. Emphasis on the cost and performance benefits especially of public cloud computing; however, tend to overshadow some of the fundamental security and privacy concerns organizations have with these computing environments. Many of the features that make cloud computing attractive can also be at odds with traditional security models and controls. Several critical pieces of technology, such as a solution for associated trust, are not yet fully realized, that directly or indirectly interrupting on successful cloud computing deployments. Determining the security of complex computer systems composed together is also a long-standing security issue that trouble large-scale computing in general, and cloud computing in particular. Attaining high-assurance qualities in implementations has been an elusive goal of computer security researchers and practitioners and, as I tried demonstrating in my paper, is also a work in progress for cloud computing. Accountability for security and privacy in public clouds remains with the organization. Organizations must ensure that any selected public cloud computing solution is configured, deployed, and managed to meet the security, privacy, and other requirements of the organization. Organizational data must be protected in a manner consistent with policies, whether in the organization’s computing center or the cloud. The organization must ensure that security and privacy controls are implemented correctly and operate as intended.
0 Source – http://www.computerweekly.com/news/2240089111/Top-five-cloud-computing-security-issues1 Customers benefit from this advanced data security layer that only they are able to decode by their direct control over it.2 The LOGICAL data security is the very new proposal disclosed in this paper only. It actually talks about an unbeatable security layer that can fit into any Cloud environment, technology and/or any Platform; because it seats within your middle layer. It gives you full proof and flexible method and option to secure your data.3 Some people may correlate it with Data Encryption, but please note that it is not data encryption.4 Calculated non-additive data is the data that is not easy to neutralize using mathematical mapping and inverse mapping.
References
[1] Latest Gartner’s Magic Quadrant for Public Cloud http://www.gartner.com/technology/reprints.do?id=1-18BC06X&ct=111213&st=sb [2] Cloud computing Thomas B Winans and John Seely Brown, Deloitte [3] Computierweekly.com News Magazine From TechTarget [4] Jounal on ‘Guidelines on Security and Privacy in Public Cloud Computing’ By Wayne Jansen and Timothy Grance of Computer Security Division, IT Leboratory, National Institute of Standards and Technology, U.S. Department of Commerce [5] An Oracle Technical Paper – Oracle Cloud Computing Authors: George Demarest, Rex Wang. [6] THE WINDOWS AZURE PROGRAMMING MODEL By DAVID CHAPPELL From DAVID CHAPPELL & ASSOCIATES. [7] An Oracle Paper – Oracle Real Application Clusters One Node: The Always Online Single-Instance Database Author: Bob Thome; Contributing Authors: Sohan DeMel. [8] An Oracle Paper in Enterprise Architecture – Achieving the Cloud Computing Vision Author – Michael Glas, Paul Andres. [9] An Oracle White Paper on Enterprise Architecture – Architectural Strategies for IT Optimization: From Silos to Clouds Author: Paul Silverstein [10] An Oracle Paper – Oracle SaaS Platform: Building On-Demand Applications Author: Milan Thanawala; Contributing Authors: Gordon Smith, Jon Dart, Shivanshu Upadhyay. [11] Platform-as-a-Service Private Cloud with Oracle Fusion Middleware Author: Mike Piech [12] An Oracle Paper – Bridging the Divide between SaaS and Enterprise Datacenters Author: Maneesh Joshi; Contributing Authors: Dain Hansen, Irem Radzik, Bharath Shashikumar [13] On-Demand Sourcing: Driving Costs Down and Value Up in a Period of Increased Business Volatility – A Hackett Research Paper By Tony Chauhan and Honorio J. Padrón III [14] ENTERPRISES ADVANCE INTO THE CLOUD: 2011 IOUG CLOUD COMPUTING SURVEY By Joseph McKendrick, Research Analyst, OIUG Produced by Unisphere Research, a Division of Information Today, Inc. [15] A paper from Microsoft – Trusworthy Computing [Privacy in the Cloud Computing Era] [16] Cloud Computing and SOA {SERVICE-ORIENTED ARCHITECTURE (SOA) SERIES, Systems Engineering at MITRE} By Geoffrey Raines [17] TECHNICAL WHITE PAPER – VMware vCloud® Director™ 1.5 Performance and Best Practices Authors: Joanna Guan, Xuwen Yu, Ritesh Tijoriwala, John Liang from VMWare
|